Powered On: October 2022
October is Cybersecurity month at College of the Canyons! Help me, help you, by reviewing a couple of these tips and tricks to keep your accounts more secure.
Passwords and Passwords and Passwords, Oh My!
by Sarah Schnittker and Mike Gunther
Passwords are an essential part of having an online presence. We use them to protect our personal accounts, our email, and our credit card information. Nearly every facet of your digital life is on the other side of a digital bridge with a grouchy, fantastical troll on the other end . That would be fine, we'd all be very happy with the troll simply doing his job, if he didn't change the rules at every bridge- this password requires a number, a special character, and a hieroglyph for good measure.

Because of this, you, like most people, likely have a string of reliable passwords- perhaps the same password with slight variations to meet the minimum requirements, or perhaps multiple passwords you cycle through until you get past the blaring 'incorrect password' log in screen. Or, you give up and reset it on the third attempt- but "your new password cannot be the same as previous passwords"… We've heard it before. According to dataprot:
53% of people rely on their memory to manage passwords.
51% of people use the same password for different accounts.
57% of people who have been hacked still haven't changed their passwords.
If you are one of these people, you are not alone.
But there are ways to do better to secure your personal information.
Passphrases are typically longer than the basic password; sometimes they have a more diverse set of requirements, or allow for a larger selection of special characters. Generally, thinking of a new password that is 14 characters long is more difficult than the average 8 character password; then they want us to throw in multiple numbers and capitals? Like passwords aren't hard enough. But these requirements are designed to protect our information from hackers and users that may have a nefarious purposes for your personal accounts. Because of this, multiple security experts encourage the use of long passphrases, such as a song lyric or line from a movie, to meet these standards.
Find out how secure your password is with this handy tool: security.org
We haven't needed to memorize a phone number since before the early 2000's. What hope do we have of memorizing a unique password for all these accounts? The answer is Password managers. If you are already using your favorite web browser's "save password" feature, you may already be familiar with the concept of a password manager. Unfortunately, that feature in web browsers was not designed securely from the outset; and parts of the digital world have become a breeding ground for different hacking methods. Your information is always at risk.
The goal of this article is not to scare you. Although the ever-changing dynamics of cyber security improves every day, it is more secure to use a password manager built for this purpose. Password Managers like LastPass, 1Password, Dashlane and a host of others, feature more than just password protection; you can store credit card numbers, private notes, addresses, and bank account information securely encrypted in a digital vault. Additionally, multi-factor authentication and password diversity provides added layers of protection.
To get started, many password manager products provide a free tier to let you experience it before you buy; this is a great way to get your feet wet with the concept of using a password manager. But after getting comfortable with the service, you'll never need to remember all those passwords again.
In summary:
- Passphrases, like a line from your favorite movie, are more secure than a password alone- and easier to remember.
- Password managers, like LastPass, are effective tools in securing the many variations of your passwords, so you don't haveto remember them all.
- You are your biggest investor, no one is more concerned about your personal information than yourself. So, take the steps to secure it!
Stop! Don't Attach That File!
by Sarah Schnittker and Mike Gunther
Email is not secure! Passwords are not secure! WHAT DO I DO!!!
If you see something unusual, STOP. Generally speaking, your colleagues are not looking to scam you; but it is always possible that their email has already been compromised. If the email looks too good to be true, it usually is.

Hacking and phishing your personal information, unlike Halloween, is not restricted to a specific season. Data that travels between computers, such as through email, is not typically encrypted by default. Even if that data doesn't contain sensitive information, anyone could get a hold of anything if you aren't careful. We have already covered passwords earlier in this newsletter (see "Passwords and Passwords and Passwords, OH MY"),. Now, it is important to cover the security of your Email and Documents.
By no means is anyone asking you not to share crucial documents through your email; email, after all, is one of the largest forms of day-to-day communication especially in a professional work setting. Email is a tool, and it is your responsibility as a user to secure and maintain that tool.
Step one is Awareness. The more you know, the more effective you can be at securing your information. That means being aware of what's fluttering through your inbox, who it is coming from, and where those links in the email might go. If you have any doubts, don't touch it.
Step two is Action; move your information into a more secure location, such as in the cloud or behind password walls. A powerful sharing tool provided to you by College of the Canyons is OneDrive. A personal cloud storage operated by Microsoft, OneDrive is one of the most secure ways to share files. Some of the key functions are as follows:
- Control: You select the specific users and their specific powers within a document, such as who has editing rights and who has authorized viewing capabilities. You are in control and can revoke user rights at any time.
- Accessibility: Your documents are accessible to you at any time, from any location, so long as you are logged in- meaning, if you go to a different desktop and log in, your information will carry with you. The same goes for your recipients.
- Collaboration: When you share a document with other users and you allow them to edit the document, you will be able to see the changes they make to the document, as they make those changes.
- Storage: 1 Terabyte isn't bottomless, per say, but it is a massive amount of digital real estate available to you provided by the college.
Step three, Repeat. The digital world is always changing, with new phishing attempts and scams becoming more convincing. It is your responsibility to take the steps best for securing your information. Our advice: Simplify your security by raising awareness, getting familiar with OneDrive, and making a plan to move your data into the cloud. Check with Computer Support Services for assistance in getting started.
4CUG Virtual Conference
By Lisa Sawyer
4CUG is the Colleague (formerly Datatel) California Community College Users Group. Their Virtual Conference takes place October 18-20 from 1:00 pm to 5:00 pm each day. The conference is free and held via zoom. All staff and faculty from the College are welcome to attend. There will be a number of Colleague sessions that may be of interest to you - and you only need to attend sessions you want. Most of the Sessions are led by employees from Colleague Schools throughout the stat along with sessions from ellucian, the company who owns Colleague.
If you are interested in attending one or more of these sessions, registration is required. Registration for the Opening Session for October 18th, 1:00 PM session, will give you full access to ALL the sessions. Once the schedule has been finalized, links will be sent to ONLY those that have registered.
Click to Register for the 4CUG 2022 Virtual Conference or go to https://mercedccd.zoom.us/meeting/register/tZwpd-qpqDsqHtXfqsTNk0MMWEG9Hlf1DqFi
After registering, you will receive a confirmation email containing information for the Opening Session. Details on other sessions will be coming soon! 4CUG is still working with Ellucian and session presenters to confirm the schedule.
Zoom + Single Sign On
by Sally Rowland and Justin Smith
Fun Fact. Zoom Single-Sign-On (aka SSO) credentials are more secure than logging in with your email credentials. Instead of utlizing your email address to login, login to ZOOM with your single-sign-on credentials.
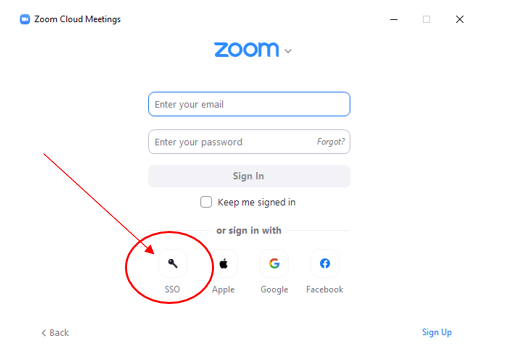
1) Simply launch zoom and click the SSO button from the login page of ZOOM:
If you are already logged in, you will have to log out of zoom first.
 |
2) Type in "CANYONSONLINE", canyons, online, with no spaces.
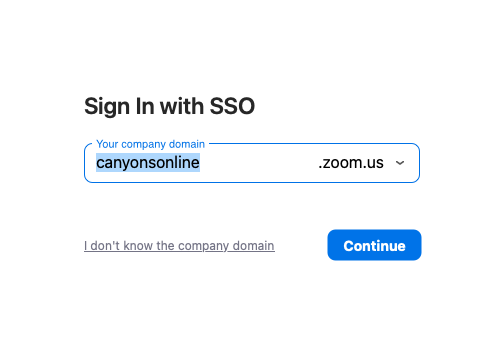 |
3) Click Continue
4) Enter your CanyonsID, along with your two-factor-authentication, and you are in!
Click here to review how to login with your Canyons ID.
5) Zoom Zoom
How Secure is My Password & Two Factor Authentication
By Justin Smith
Have you ever woken up in the middle of the night covered in sweat asking yourself, "how secure is my password?". Neither have I, but if you'd like to test-drive your credentials anyway, head on over to this website:
Long story short, your password generates an "encrypted key" whenever it is typed. That key is actually what is utilized to authenticate your username. The more characters, the better!
All kidding aside, two factor authentication is one of the easiest ways to add a layer of security to an account. Review your account settings to whatever you are logging into, to see if they support it.


 My Canyons
My Canyons  Canvas
Canvas