Powered On: May 2024
Fact or Fiction: The Myths of Cyber Security
by Sarah Schnittker and Michael Gunther
Exploring the Expanded District Resources Page
by Scott McAfee
The District Accessibility Resources page has been expanded, and it's your go-to source for everything related to accessibility in our district! Part of this recent expansion includes new, accessible templates for Office, Word, and Excel, which will help ensure that your digital content is structurally accessible from the very beginning. You'll also discover a wealth of new information on best practices for creating accessible PowerPoint, PDF, and Word documents, making it easier than ever to create content that everyone in our campus community can enjoy.
When considering digital or technology purchases, it's essential to request a Voluntary Product Accessibility Template (VPAT) from the vendor. This document, which must be completed by the vendor prior to purchasing approval, is a crucial step in the purchasing process for all software and hardware-based products. The information provided in the VPAT will guide our decision-making and ensure that we prioritize accessibility, fulfilling our commitment to acquiring 508 compliant tools and technology. By adhering to the VPAT process, we demonstrate our support not only for diversity, equity, and inclusion, but also compliance with BP 3725 and AP 3725, which outline our policies on Information and Communications Technology Accessibility and Acceptable Use. This proactive approach helps us maintain an inclusive and accessible digital environment for our entire campus community.
The District Accessibility Resources page is also filled with a variety of other helpful information and resources designed to support our commitment to accessibility. I encourage you to take some time to explore the page and familiarize yourself with the tools and information available. If you have any questions or need assistance with the VPAT process, District accessibility, or 508 compliance, please don't hesitate to reach out to Scott McAfee, Access Coordinator. We are here to support you in making accessibility a key consideration in all aspects of your work.
Hardware Hygiene
by Carlo Cannavale
When I step foot into my shower each morning, I ask myself the same question.... "Why does my wife have twenty different bottles of shampoos, conditioners, body washes, body scrubs, etc?". As I reach for my one bottle that science has magically figured out how to cram shampoo, conditioner and body wash into, I'm reminded how important personal hygiene is for our health and happiness. Hygiene for your tech is equally important. Take a quick moment and look at your keyboard. I mean really look at it. Look at the keys. Look between the keys. What about your mouse? What about under your mouse??? I'm willing to bet it's not a pretty sight and probably much worse than you thought. Aside from the general grime that builds up over time and looks unsightly, crumbs, dust and oil can build up and affect how your peripherals perform. Keeping your peripherals clean can improve their performance and extend their life. It only takes a few minutes and the supplies you'll need are inexpensive and easy to find. You may even them already.
You'll need the following:
- Isopropyl Alcohol (70% or higher)
- Cotton Swabs/small brush
- Microfiber Towel/Cloth
- Canned compressed air
- Screen cleaner spray
Power off or unplug your keyboard (if wired) and take it out outside. Use the compressed air and blow in between the keys. Hold the keyboard upside as you spray to allow gravity to help you clear out any debris. Once done, take it back inside. From here, pour a small amount of alcohol on your cleaning cloth and wipe down the keyboard, making sure to get in between the keys and the underside of the keyboard. Add some more alcohol onto the cloth if needed and begin wiping down the mouse. If it has any removable plates or covers, remove them. Wipe all around as well the bottom of the mouse which attracts the most grime from your desk. Use the cotton swabs or brush to get into the crevices. Alcohol does a great job of breaking down the grime and disinfecting the surfaces. It also evaporates quickly which makes it great to use on electronics. To clean your monitors, you can use alcohol to clean the outer bezels and back of the monitor but you will want to use a special cleaner designed for screens. Never use Windex as ammonia can damage the screen's surface. Spray the cleaner onto a microfiber cloth and gently wipe down your screen. Make sure to also check for any dust build up on the vents of your laptop or desktop as that could cause your device to overheat. Taking these simple steps will insure your devices and peripherals not only look good but help to extend their lives and keep them performing well for a long time.
If you need help cleaning a laptop keyboard, feel free to stop by one of our I.T. offices and ask one of our technicians for assistance.
Virtual Meeting Tips
Looking for ways to get the most out of your virtual meetings? Dipesh Jain, leader of sales and marketing teams at Magic EdTech, has some helpful tips for you. In his article, "Virtually Possible", Jain outlines many ways in which you can maximize the benefits of your digital meetings.
His tips include:
- "Set a clear agenda."
- "Manage your time."
- "Adhere to the allocated duration."
- "Aim for meetings to conclude a few minutes before the half-hour or hour mark."
- "Boost engagement."
- "Polls, question-and-answer sessions, and breakout room help to increase engagement"
- "Don't get hijacked."
- "Diplomatically intervene if someone is monopolizing your meeting"
- "Agree on action items."
- "Conclude with actionable tasks."
- "Identify, document, and delegate tasks."
- …and more!
To read more about Jain's virtual meeting tips, follow this link:
https://www.costcoconnection.com/april_2024/page3.html
Microsoft OneNote features to boost your note-taking productivity
by Santhy Chandran
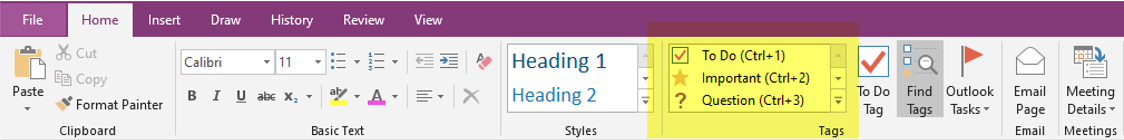
1. Tags
Tags are a way to categorize and prioritize notes in OneNote. With tags, you can quickly return to important items or filter on notes you'd like to share with others. You can tag anything from a single line of text to an entire paragraph.
In order to add a tag
- Place the cursor at the beginning of the line of text you want to tag
- Home>Tags>Select the appropriate tag from the drop-down list.
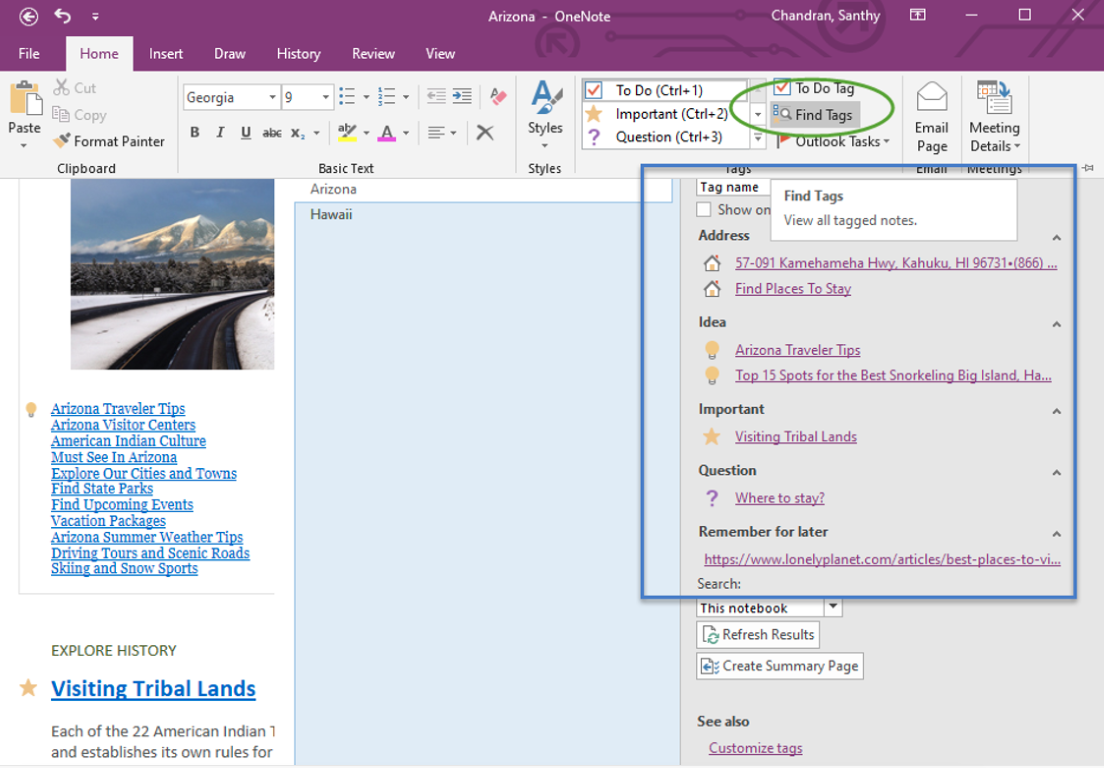
You can add tags as you fill the notes. Tags are really powerful. To find your tag, click Home>Find Tags. It will give you a list of all the places you have tagged. Tagging can save you time as your one note continues to grow.
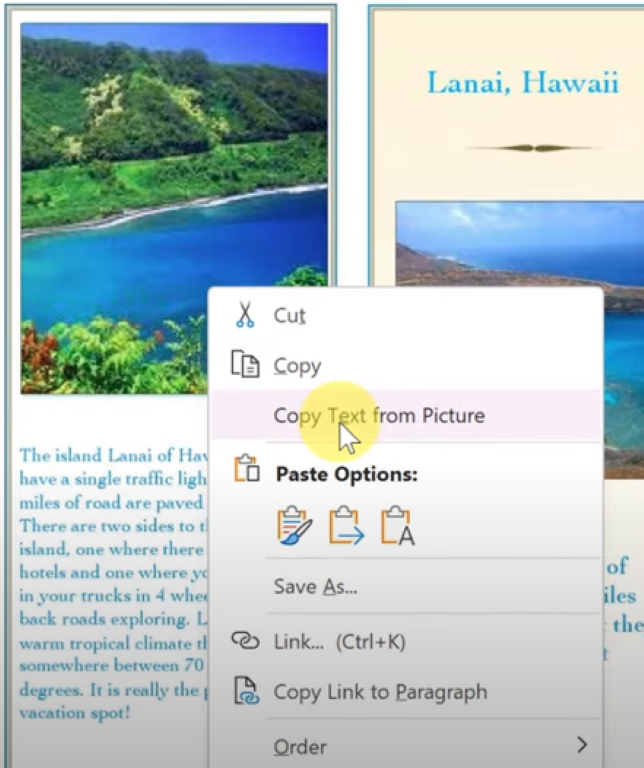
2. Copy text from picture
OneNote supports Optical Character Recognition (OCR), which lets you copy text from pictures or scanned images and paste it into your notes for editing or formatting..
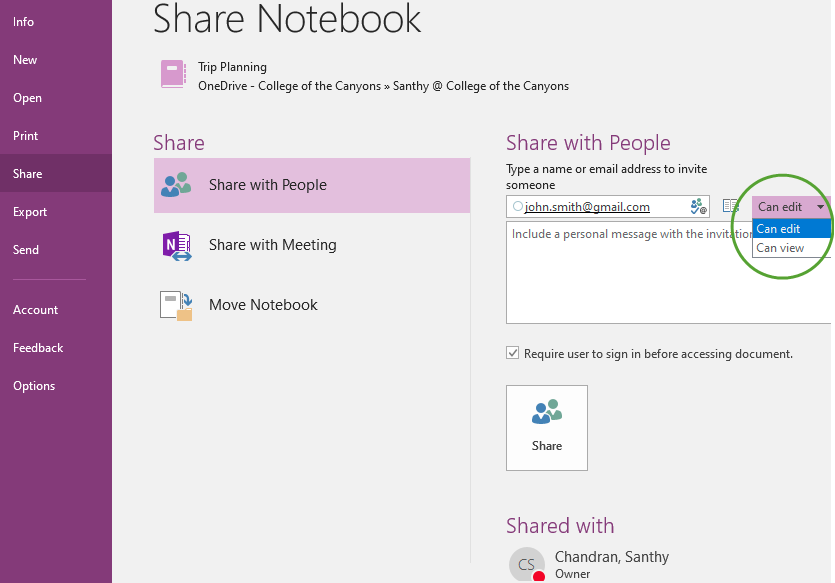
3. Share and collaborate in one note.
You can share an entire notebook with other people and allow each invited notebook participant to view or fully edit your notes.
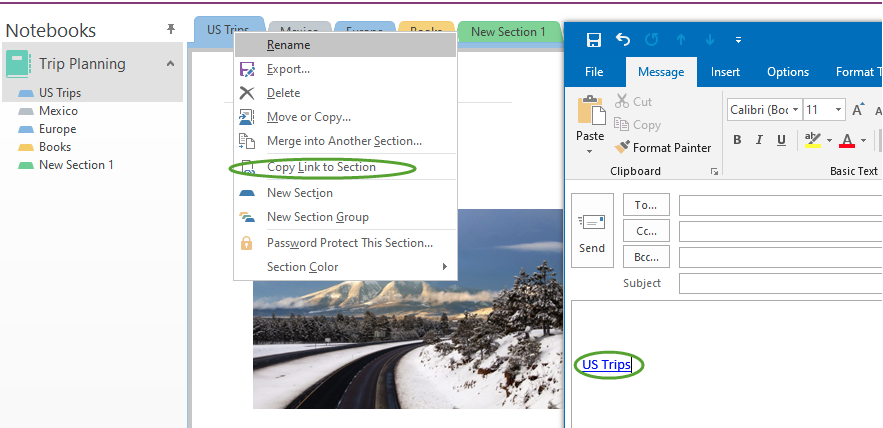
Emailing link to a section to people who is already part of your settings using Section>Copy Link to Section


 My Canyons
My Canyons  Canvas
Canvas