Powered On: Oct 2023
ICE CREAM with I.T.
Jim Temple, Vice President of Technology, will be hosting another open office hour on 10/26 from 2:30 to 3:30. Stop by to chat with Jim and have some ice cream.
Thursday 10/26 2:30PM - 3:30PM
Cybersecurity Awareness Month
by Mayra Cuellar
Immersed within the digital realm, it's crucial to stay vigilant and informed about the tools and strategies available for managing cyber risks effectively. October is Cybersecurity Awareness Month which is designed to empower individuals to safeguard themselves and make informed choices in their professional, educational, and personal online activities.
We encourage you to incorporate these 4 simple steps:
- Use strong passwords and a password manager: Creating, storing and remembering passwords can be a pain for all of us online, but the truth is that passwords are your first line of defense against cybercriminals and data breaches. Also, it has never been easier to maintain your passwords with free, simple-to-use password managers. With a few moments of forethought today, you can stay safe online for years to come.
- Turn on multifactor authentication (MFA): Multi-factor authentication is sometimes called two-factor authentication or two-step verification, and it is often abbreviated to MFA. No matter what you call it, multi-factor authentication is a cybersecurity measure for an account that requires anyone logging in to prove their identity multiple ways. Typically, you will enter your username, password, and then prove your identity some other way, like with a fingerprint or by responding to a text message.
- Recognize & report phishing: Phishing is when hackers use fake emails, social media posts or direct messages with the goal of luring you to click on a bad link or download a malicious attachment. If you click on a phishing link or file, you can hand over your personal information to the cybercriminals. A phishing scheme can also install malware onto your device. Verify the authenticity of requests by contacting the individual or organization through a trusted channel. Report phishing attempts to the appropriate authorities or IT department.
- Update software: If you install the latest updates for devices, software, and apps, not only are you getting the best security available, but you also ensure that you get access to the latest features and upgrades. However, you can only benefit if you update! Don't fret, updating software is easy, and you can even make it automatic.
Become a Cybersecurity Awareness Month partner by helping to promote a safer, more secure, and more trusted internet.
Thirsty for more? Check out https://www.cisa.gov/cybersecurity-awareness-month
Cybersecurity Awareness Training
by Hsiawen Hull
When I say October, I imagine it conjures images of fall leaves, trick-or-treating and pumpkin spice lattes! But for security nerds like our Information Security team, October is the omen of Cybersecurity month!!! Like last year, my team has some excitement in store for everyone. We will be offering an updated and expanded series of workshops including the State of Cybersecurity, Cybersecurity Best Practices, and our latest workshop where we delve into the scary depth of Enrollment Fraud! In addition, fan-favorites, like the annual Phishing Tournament, will be returning this year for staff AND students.
Sessions available in October
State of Cybersecurity
This series is intended to provide insight into what District IT is doing to keep our data, employees, and students safe from malicious cyber-attacks. Learn about the ever-changing landscape of Cybersecurity and how threat actors have evolved from stealing your passwords to ransomware attacks on some of the largest corporations in the country. This series will also highlight how these incidents impact you and your information directly.
Thursday, October 5th and Monday, October 16th @ 10:00AM
Information Security Best Practices
An overview of Information Security, what it is, why it's important and what you need to do to keep yourself and your data safe, both personally and professionally. We will be discussing best practices and the steps you can take to improve your digital security.
Wednesday, October 11th and Wednesday, October 25th @ 1:00PM
Faculty vs. Enrollment Fraud
A lingering side effect of the Covid pandemic has been a sharp increase in the number of fraudulent enrollments impacting the California Community College system. While we don't always know WHY they're enrolling in classes, we do know that fraudsters are coming to us at an alarming rate. Learn how COC Faculty are on the front lines, helping us identify fraudulent students and how with their help we've been able to block more than 250 fraudulent enrollments in the last 3 semesters ALONE. More importantly, what can you do to help and what does all this have to do with Dinosaurs?
Thursday, October 26th and Monday October 30th @ 11:00AM
Avast! Be Wary of QR Code Phishing
by Sarah Schnittker and Michael Gunther
One might use the same words to describe both the internet and the ocean: vast, sprawling, an endless expanse. Although an excellent tool, the uncharted waters of the internet pose many dangers to users. Scammers have been targeting students in higher education for years, but we're seeing spikes of "Phisherman" looking for your personal data.

The latest siege is utilizing QR codes sent to you in your email to steal your information. The QR codes in these emails are meant to make you scan them with your mobile device, where you may have less security protection than your computer. This way, the attacker can bypass the detection mechanisms and lure you into their trap.
We want to remind you to be vigilant and careful when you receive any email that asks you to scan a QR code or click on a link. Do not trust any email that claims to be from a bank, a government agency, or a company that you do not recognize or do business with. Always check the sender's address, the spelling, grammar, tone, and urgency of the message. If something seems suspicious or too good to be true, it probably is.
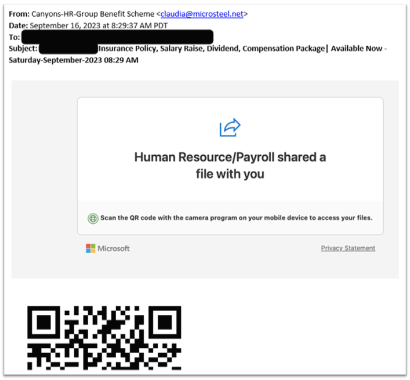
Of course, QR codes are not the only way scammers have tried phishing emails at College of the Canyons. Your outlook email is a vital part of your communication with district resources; but recently, we've been experiencing a crashing wave of new reports regarding suspected phishing attempts. Phishing can take many different forms, but the goal is to get access to your personal information, passwords, or credit card information. Here are the top three tips to keeping your information secure from phishing attempts:
- Mouse over external links before clicking them. This will allow you to see where the link may be going, and if a bad actor might bypass our protectors.
- NEVER respond to requests for Gift Cards, Credit Card information, or your personal information via email; especially if the requestor is an external email or you do not recognize the request. If possible, call the department to confirm it is a real request, or report it through your outlook email.
- ALWAYS report emails you suspect to be Phishing. Successful reports often allow us to preemptively target and remove cyber security risks. If you are unsure, please make the Technology team aware by forwarding your concern to the Help Desk.
Security Event Shoutouts
by Sarah Schnittker
For some, when we look back on the recent summer, we reminisce about the warmer weather, afternoons by the poolside, and perhaps some well-deserved time off. But like most of you who worked during the summer months, the IIS team spent the summer combatting potential threats and insecurities within our network. Perhaps more importantly, College of the Canyons has been an inspiration to districts across Southern California on creating a more secure digital learning environment. This is largely due to the combined efforts of Hsiawen and his team.
On July 27th, College of the Canyons participated in the planning and execution of a region-wide conference emphasizing Security Best Practices. With a surprising turnout of 32 different districts, the day was spent discussing how to identify weaknesses in cybersecurity infrastructure. It was an engaging event with positive results. Many of the attendees were able to network with their peers from surrounding colleges and industry security experts to share best practices that can be deployed to protect college resources and students across California.

On September 8th, the Technology team hosed a virtual state-wide digital workshop to discuss the purchasing process for software with emphasis on how to address security when acquiring new products. A staggering 38 different districts attended to discuss how to improve the security of their district information and the HECVAT evaluation process. Special thanks to Michael Gunther for leading this workshop.
On September 13th, our Technology leadership was invited to the Microsoft Cyber Security summit. Hsiawen Hull represented College of the Canyons, while speaking on the Microsoft campus in Silicon Valley about our district's security journey to an audience of education professionals and Microsoft leadership.
On October 19th, coming up, Hsiawen Hull will also be discussing these same points on the Microsoft Education National office hours-a podcast that focuses on Microsoft technologies, with an academic lens. Tune in on the Microsoft Office Hours YouTube channel, here.
A Smarter Picture
by Justin Smith
Technology has a funny way of cycling back around. This past week the topic of smart pictures and televisions came up twice in the same day! Both times it was recognized as a brand-new invention and still viewed as innovative. Samsung first released the frame TV in 2017 with a matte finish screen, auto-brightness features, and a digital wallpaper. When the TV is "off" it can display art and mimic a static piece of art. It can even display a faux mat board to help accentuate your choice of art. This is by far the most advanced smart picture frame I've seen to date. As if that all isn't enough, they also have custom boarders to further dress your walls to perfection. With a custom boarder clipped onto this model, it makes the still image look like an actual framed piece of art! Keep an eye out for these unique TVs in the wild. They are available in a variety of sizes ranging from 32 inches, all the way up to 85 inches.
Enterprise Applications Document Library
by Lisa Sawyer
Have you ever wondered how to do something in Colleague or Informer? We may have the answer for you in our Enterprise Applications Document Library. It can be found on the COC Intranet by going to https://intranet.canyons.edu/departments/it/applications/docs.php. Although there are a number of documents in the library, some that may be of interest to you are:
- Colleague User Guide
- Colleague Overview Presentation Handout
- Informer - General Instructions
- Printing and Exporting a Screen in Colleague
- Saving Your Frequently Used Forms in Colleague
Laugh it up, Chuckles
What was the spider doing on the computer?... He was making a web-site!


 My Canyons
My Canyons  Canvas
Canvas